Make sure that 'Enable IEEE 802.1x authentication' has a check mark next to it. Click Additional Settings. In the Additional Settings screen make sure that 'Specify Authentication Mode' is checked. From the drop down right below that select 'User or computer authentication'. Make sure that 'Enable IEEE 802.1x authentication' has a check mark next to it. Click Additional Settings. In the Additional Settings screen make sure that 'Specify Authentication Mode' is checked. From the drop down right below that select 'User or computer authentication'. Enabling 802.1x authentication on Dell EMC Networking Force10 switches. Update your Windows 10 computer for a successful connection to the campus wired network. Follow these steps to check your network setting (802.1xAuthentication). You need to be the administrator on your computer to perform the following steps.
When using 802.1x authentication (wired or wireless) on a Windows computer joined to an Active Directory Domain, Windows Group Policies Objects (GPO) can deploy the Native Supplicant configuration. The native supplicant can use different authentication methods, the common method being PEAP/MSCHAPv2 which uses Username and Password authentication. Slightly less common due to the perceived complexity is EAP-TLS which uses computer and/or user certificates.
This blog post describes the configuration of PEAP/MSCHAPv2, this requires only valid username and password for successful authentication.
Group Policy Configuration
- Create a new GPO (or if required modify an existing policy) link the policy to an OU that the computers will inherit the policy configuration
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > System Services
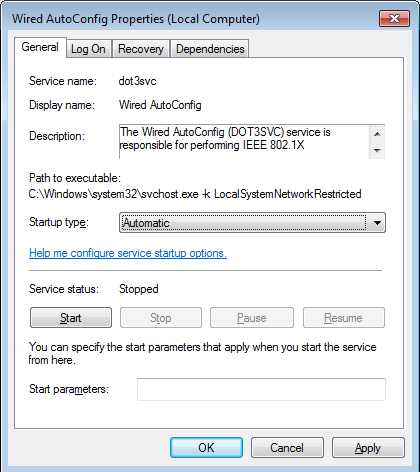
- Locate the Wired AutoConfig service and double click to edit
- Select Define this policy setting
- Ensure Automatic is selected as startup mode
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Wired Network (IEEE 802.3) Policies
- Right click and select Create A New Wired Network Policy for Windows Vista and Later Releases
- Name the policy appropriately, e.g. Wired Authentication Policy
- Click the Security tab
- Select the desired Authentication Mode it would be recommended to use User or Computer authentication, in order for both the Computer and User to be authenticated in order to grant network access in order to process Computer and User Group Policies.
- Select the authentication method, e.g. Microsoft: Protected EAP (PEAP)
- Click Properties
- Ensure Validate server certificate is selected
- Select the Trusted Root Certification Authorities certificate is selected (this certificate must be present in the Trusted Root certificate store of the RADIUS server and the client computer)
- Ensure the authentication method is Secured password (EAP-MSCHAPv2)
- Leave other settings as default
- Click Ok
- Click Ok to complete the configuration
Verification
- Apply the GPO to a test computer
- Open the Services MMC and check the status of the Wired AutoConfig service, this needs to be running
- Open the Local Area Connection Properties, if the service is running the Authentication tab will be present
Notice that configuration is not possible as this settings have been applied from the GPO previous configured.
If the Wired AutoConfig service is not started, the Authentication tab will not be present.
Confirm the Trusted Root Certificate is present in the Local Computer certificate store. This certificate should automatically be present if joined to the Active Directory Domain.
Assuming the RADIUS server is configured correctly and the same Trusted Root Certificate is trusted by the Computer and the RADIUS server. Refer to this previous blogpost that describes how to configure Cisco ISE for Wired 802.1x authentication.
Update 10/1/2018 – Check out my latest post Part 5 below. You may be able to skip all of the other stuff!!
The Links first so you don’t have to scroll so far. These are also on the menu at top for easy access. Since I ended up with so much content for this topic, I felt that it warranted a landing page. Hopefully you will be able to easily navigate through these topics and find some useful nuggets to save yourself some headaches down the road.
Part 1 – Building an 802.1x Computer Authentication Script
Part 2 – Building an 802.1x Enabled WinPE Boot Image
Part 3 – Integrating 802.1x Authentication into a Bare Metal Task Sequence
Part 4 – Integrating 802.1x Authentication into an In-Place Upgrade Task Sequence
Part 5 – Dynamic Whitelisting using the Cisco ISE External RESTful Service
Bonus – Tips and Tricks

If find yourself on this page, you have either 1) made a wrong turn and ended up here by mistake or 2) are tasked with getting IEEE 802.1x Authentication to play nice with your Windows Operating System Deployment. If its option 1, save yourself! Go look for some cat videos or something. You don’t want to be here, trust me! If its option 2, welcome to the club. Come on in and make yourself comfortable, it’s gonna be a long ride. For my team, this has been one of the most frustrating things to work with/around in our environment. My goal with this series (Yes, this is going to take a few sheets of paper) is to share what I’ve learned over the past few years and the discoveries I’ve made. I’m using ConfigMgr/SCCM with Cisco ISE providing our 802.1x protection, so all of the following is geared toward SCCM Task Sequences and the integration between the Windows ADK, WinPE, Wired AutoConfig, Windows 10 and 802.1x. Oh, and Cisco ISE.
There are multiple ways to configure your network interface for 802.1x authentication and the options you choose will depend on how your 802.1x protection service is configured. For my environment, Cisco ISE will accept either valid domain user credentials or a valid machine certificate. For several years, we used a script to import an 802.1x user authentication profile along with a service account and password to configure authentication on the LAN interface. We soon realized that we would have to update our WinPE Boot Image every 3 months since we are required to reset passwords every 3 months. This is a hassle that we wanted to do away with. So, I developed the solutions that follow to help us switch from user authentication to computer authentication.
Now, you may be asking why we would do this and not just build machines in a secure build room. I’m so glad you asked. Because we hate ourselves and wanted to make things difficult!! Honestly, we’ve done that for quite some time and it has worked pretty well. As we are moving from Windows 7 to Windows 10 with an eye on Modern Management and Windows AutoPilot, we wanted to move to a user-driven imaging/upgrade model. A user can initiate an upgrade from their desk and minimize the manpower required to support the effort.
If you want more info about what 802.1x Authentication is or how to implement it, you won’t find that here. I just won’t come close to explaining it properly, so if you want to know more, I’m sure someone smarter than me has already geeked-out writing a nice article about the wonders of 802.1x authentication and why it’s the most amazing security protocol and such. I just want to know how to get around it so I can get machines imaged and out the door!
Network Authentication Failed Windows 10
17,259