You receive error message 0x80090016 or error message 0x8009000f when you try to schedule a profile
- What Does Code 0x80090016 Mean
- Windows Error Code 0x80090016
- Microsoft Error Code 0x80090016
- Return Code 0x80090016
- A couple of days ago, people started reporting a Windows Store error code: 0x80070216. In most of the cases, it shows up when people attempt to install or update Kodi, but a thorough error analysis revealed that that the bug is not Kodi specific.
- Windows 10 from a Windows 7 upgrade. Windows 7 system backups worked fine, stopped after migration. Get the following error: Also see lots of errors in the event viewer about VSS issues Attaching event viewer export: evntvwr.zip Interesting one is the volume shadow copy service times out and then stops.
When you attempt to schedule a profile you may receive either of the following error messages:
- The new task has been created, but may not run because the account information could not be set. The specific error is: 0x80090016: Keyset does not exist.
or
- The new task has been created, but may not run because the account information could not be set. The specific error is: 0x8009000f: Object already exists.
The following Microsoft fix may help to resolve that Windows error:
- Stop the 'Cryptographic Services' service running on your computer
- Open File Explorer and select View > Options > 'Change folder and search options'.
0x80090016 - NTEBADKEYSET Keyset does not exist winerror.h Basically, the machine key providers were corrupted because of which IIS was not able to decrypt the password set for Application pool. Due to this AppPool was throwing the above-mentioned error.
- Select the View tab and in Advanced settings, select 'Show hidden files, folders, and drives' and click on OK button.
This article helps you understand and troubleshoot issues that you may encounter when you set up co-management by auto-enrolling existing Configuration Manager-managed devices into Intune.
In this scenario, you can continue to manage Windows 10 devices by using Configuration Manager, or you can selectively move workloads to Microsoft Intune as you want. For more information about how to configure workloads, see Support Tip: Configuring workloads in a co-managed environment.
Original product version: Microsoft Intune
Original KB number: 4519160
Before you start
Before you start troubleshooting, it's important to collect some basic information about the issue and make sure that you follow all required configuration steps. It helps you better understand the problem and reduce the time to find a resolution. To do this, follow this checklist of pre-troubleshooting questions:
- Did you have the required permissions and roles to configure co-management?
- Which Azure AD hybrid identity option did you select?
- What is your current MDM authority?
- Did you install and configure Azure AD Connect?
- Did you assign an Azure AD Premium license to the UPN that you used for configuration?
- Did you assign Intune licenses to the users?
- Did you configure hybrid Azure AD join for managed domains or federated domains?
- Did you configure the Configuration Manager client agent settings for hybrid Azure AD join?
- Did you configure auto-enrollment in your Intune tenant?
- Did you enable co-management in Configuration Manager?
Most issues occur because one or more of these steps were not completed. If you find that a step was skipped or was not completed successfully, check the details of each step, or see the following tutorial: Enable co-management for existing Configuration Manager clients.
Use the following log file on Windows 10 devices to troubleshoot co-management issues on the client:
%WinDir%CCMlogsCoManagementHandler.log
Troubleshooting hybrid Azure AD configuration
If you are experiencing issues that affect either Azure AD hybrid identity or Azure AD connect, refer to the following troubleshooting guides:
If you are experiencing issues that affect hybrid Azure AD join for managed domains or federated domains, refer to the following troubleshooting guides:
Common issues
Clients did not receive the policy from Configuration Manager management point to start the registration process with Azure AD and Intune
This issue occurs because of an issue in Configuration Manager and not Intune. You can use the client log files to troubleshoot such issues.
The Configuration Manager client is installed. However, the device isn't registering with Azure AD and no errors are seen
This issue usually occurs because the Configuration Manager client agent settings aren't configured to direct the clients to register.
To fix the issue, verify that you follow the steps in Configure Client Settings to direct clients register with Azure AD.
The Configuration Manager client is installed and the device is registered successfully with Azure AD. However, the device isn't automatically enrolled in Intune and no errors are seen
This issue usually occurs when auto-enrollment is misconfigured in your Intune tenant under Azure Active Directory > Mobility (MDM and MAM) > Microsoft Intune.
To fix the issue, follow the steps in Configure auto-enrollment of devices to Intune.
You can't locate the co-management node under Administration > Cloud Services in the Configuration Manager console
This issue occurs if your version of Configuration Manager is earlier than version 1906.
To fix the issue, update Configuration Manager to version 1906 or a later version.
Hybrid Azure AD joined devices fail to enroll and generate error 0x8018002a
When this issue occurs, you also notice the following symptoms:
The following error message is logged in the Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostic-Provider > Admin log in the Event Viewer:
Auto MDM Enroll: Failed (Unknown Win32 Error code: 0x8018002a)
The following error message is logged in Applications and Services Logs > Microsoft > Windows > AAD > Operational log in the Event Viewer:
Error: 0xCAA2000C The request requires user interaction.
Code: interaction_required
Description: AADSTS50076: Due to a configuration change made by your administrator, or because you moved to a new location, you must use multi-factor authentication to access.
This issue occurs when multi-factor authentication (MFA) is Enforced. It prevents the Configuration Manager client agent from enrolling the device by using the logged-in user credentials.
Note
There is a difference between having MFA Enabled and Enforced. For more information about the difference, see Azure AD Multi-Factor Authentication user states. This scenario works by having MFA Enabled but not having MFA Enforced.
To fix the issue, use one of the following methods:
- Set MFA to Enabled but not Enforced. For more information, see Set up multi-factor authentication.
- Temporarily disable MFA during enrollment in Trusted IPs.
Devices fail to sync after auto-enrollment
What Does Code 0x80090016 Mean
Starting in Configuration Manager version 1906, a co-managed device running Windows 10 version 1803 or a later version automatically enrolls to the Microsoft Intune service based on its Azure Active Directory (Azure AD) device tokens. However, the device fails to sync, and you receive the following error message in Settings > Accounts > Access work or school:
Sync wasn't fully successful because we weren't able to verify your credentials. Select Sync to sign in and try again.
When this issue occurs, the following error message is logged in Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostic-Provider > Admin log in the Event Viewer:
MDM Session: Failed to get AAD Token for sync session User Token: (Unknown Win32 Error code: 0xcaa2000c) Device Token: (Incorrect function).
The following error message is logged in Applications and Services Logs > Microsoft > Windows > AAD > Operational log in the Event Viewer:
Error: 0xCAA2000C The request requires user interaction.
Code: interaction_required
Description: AADSTS50076: Due to a configuration change made by your administrator, or because you moved to a new location, you must use multi-factor authentication to access.
This issue occurs when MFA is Enabled or Enforced, or Azure AD Conditional Access policies that require MFA are applied to all cloud apps. It prevents user association with the device in the portal.
To fix the issue, use one of the following methods:
- If MFA is Enabled or Enforced:
- Set MFA to Disabled. For more information, see Turn off legacy per-user MFA.
- Bypass MFA by using Trusted IPs.
- If Azure AD Conditional Access policies are used, exclude the Microsoft Intune app from the policies that require MFA to allow device sync by using the user credentials.
A hybrid Azure AD joined Windows 10 device fails to enroll in Intune with error 0x800706D9 or 0x80180023
When this issue occurs, you typically see the following error message in Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostic-Provider > Admin log in the Event Viewer:
MDM Enroll: OMA-DM client configuration failed. RAWResult: (0x800706D9) Result: (Unknown Win32 Error code: 0x80180023).
MDM Enroll: Provisioning failed. Result: (Unknown Win32 Error code: 0x80180023).
MDM Enroll: Failed (Unknown Win32 Error code: 0x80180023)
Auto MDM Enroll: Device Credential (0x80180023), Failed (%2)
MDM Unenroll: Error sending unenroll alert to server. Result: (Incorrect function.).
MDM Unenroll: Changing dmwappushservice startup type to demand-start failed. Result: (The specified service does not exist as an installed service.)
This issue occurs if the dmwappushservice service is missing from the device. To verify, run services.msc to look for this service.
To fix this issue, follow these steps:
On a working device that runs the same version of Windows 10 as the affected device, export the following registry key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesdmwappushserviceLog on to the affected device as a local administrator, copy the .reg file to the affected device, and then merge it with the local registry.
Restart the affected device.
Delete the old Azure AD registration, and then update Group Policy.
Restart the affected device again. The device should be able to register with Azure AD and enroll in Intune automatically.
Hybrid Azure AD join fails in a managed domain with error 0x801c03f2
When you run dsregcmd /status from a command prompt on the device, you can see that it's domain joined but not hybrid Azure AD joined. The following error message is logged in Application and Service Logs > Microsoft > Windows > User Device Registration > Admin log in the Event Viewer:
Server response was: {'ErrorType':'DirectoryError','Message':'The public key user certificate is not found on the device object with id <DeviceID>'.
This issue occurs in one of the following situations:
- The device object is missing in Azure AD.
- The
Usercertificateattribute doesn't have the device certificate in the on-premises AD or Azure AD.
For Windows 10 device registration to work in a managed domain, the device object must be synced first. The registration process works as follows:
- The Windows 10 device starts for the first time after it's on-premises domain joined.
- Device registration is triggered and a certificate request is created.
- When the request is created, the public key of the certificate is published in the on-premises AD for the device object. This updates the
Usercertificateattribute on the device objects. At the same time, the signed device registration request is sent to Azure AD. - The registration fails because Azure AD can't authenticate the device object or verify the signed request.
- The next time that the sync cycle runs, it finds the device object that has the
Usercertificateattribute populated, and syncs the device object to Azure AD. - The next time the registration service is triggered (this runs every hour), the device will send a new request that's signed by the private key.
- Azure verifies the signature on the request by using the public certificate that was received from the on-premises domain during the sync cycle. If Azure AD can verify the signature on the request, the device registration succeeds.
To fix the issue, follow these steps:

In the on-premises AD, make sure that the
Usercertificateattribute is populated and has the correct certificate.Check the back-end device object and make sure that the
Usercertificateattribute exists and is populated.If the certificate is missing, or someone deleted the certificate from the on-premises AD (which, in turn deletes the certificate from Azure AD), the device registration fails. To fix this issue, do the following on the client device:
Open an elevated Command Prompt window, and then run the following command:
Run
certlm.mscto open the local computer certificate store.Make sure that the computer certificate that's issued by MS-Organization-Access is deleted.
Restart the client device to trigger a fresh device registration.
After the device is restarted, make sure that the new certificate public key is updated on the device object in the on-premises AD. If there are multiple domain controllers, make sure that the attribute is replicated to all domain controllers.
Trigger a delta sync on the Azure AD Connect server.
After the sync is completed, you can trigger device registration by restarting the client, running the
dsregcmd /debugcommand, or running the scheduled task Automatic-Device-Join under Workplace Join.
Automatic device registration fails with error 0x80280036
When this issue occurs, the following error message is logged in Application and Service Logs > Microsoft > Windows > User Device Registration > Admin log in the Event Viewer:
DeviceRegistrationApi::BeginJoin failed with error code: 0x80280036
Description:
The initialization of the join request failed with exit code: The TPM is attempting to execute a command only available when in FIPS mode.
This issue occurs if the TPM chip on the client device has FIPS mode enabled. FIPS mode isn't supported or recommended for Azure device registration. For more information, see Why We're Not Recommending 'FIPS Mode' Anymore.
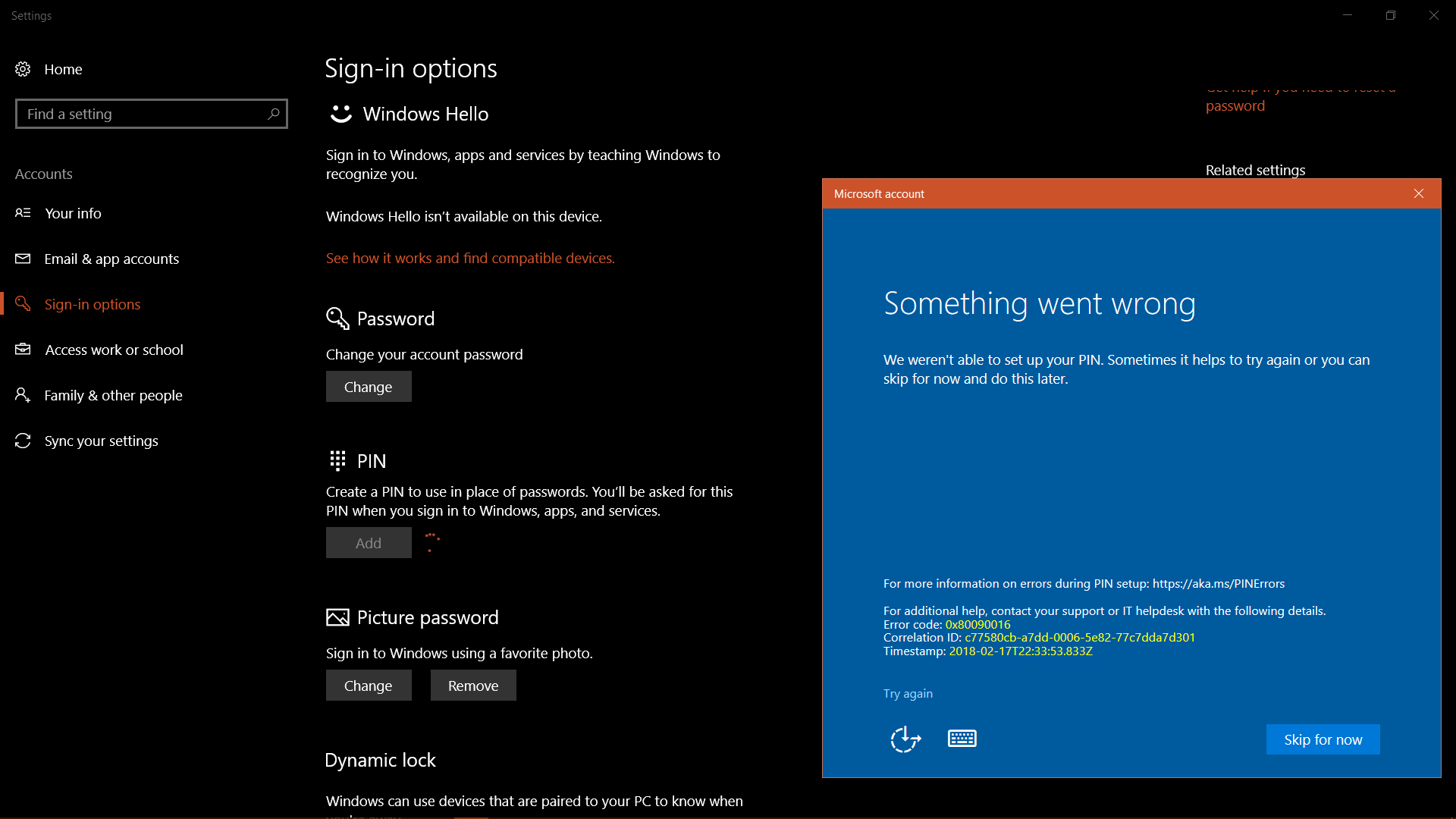
Hybrid Azure AD join fails with error 0x80090016
Hybrid Azure AD registration of a Windows 10 device fails, and you receive the following error message:
Something went wrong. Confirm you are using the correct sign-in information and that your organization uses this feature. You can try to do this again or contact your system administrator with the error code 0x80090016
The error message of 0x80090016 is Keyset does not exist. This means that the device registration could not save the device key because the TPM keys were not accessible.
This issue occurs if Windows isn't the owner of the TPM. Starting with Windows 10, the operating system automatically initializes and takes ownership of the TPM. However, if this process fails, Windows won't be the owner and will result in the issue.
To fix this issue, clear the TPM and restart the client device. To clear the TPM, follow these steps:
Open the Windows Security app.
Select Device security.
Select Security processor details.
Select Security processor troubleshooting.
Click Clear TPM.
Important
Before you clear the TPM, be aware of the following:
- Clearing TPM can result in data loss. You will lose all created keys that are associated with the TPM and data that's protected by those keys, such as a virtual smart card, a logon PIN or BitLocker keys.
- If BitLocker is enabled on the device, make sure that you disable BitLocker before you clear the TPM.
- Make sure that you have a backup and recovery method for any data that's protected or encrypted by the TPM.
Restart the device when you are prompted.
Note
During the restart, you may be prompted by the UEFI to press a button to confirm that you want to clear the TPM. After the restart is completed, the TPM will be automatically prepared for use by Windows 10.
After the device restarts, hybrid Azure AD join should be successful. To verify, run dsregcmd /status command at a command prompt. The following result indicates a successful join:
AzureAdJoined : YES
DomainName : <on-prem Domain name>
For more information, see Troubleshoot the TPM.
More information
For more information about troubleshooting co-management issues, see the following articles:
Windows Error Code 0x80090016
For more information about Intune and Configuration Manager co-management, see the following articles:
If you have a question or want to get involved with our online community, visit our Intune forum.

Microsoft Error Code 0x80090016
You can also submit feedback and ideas to the Intune development team through our user voice site.
Return Code 0x80090016
If all else fails and you'd like to open a support case with the Intune support team, see How to get support for Microsoft Intune.
